Proxy Design Pattern
Intent
From the client’s point of view, the proxy behaves just like the actual object.
Typical Variations
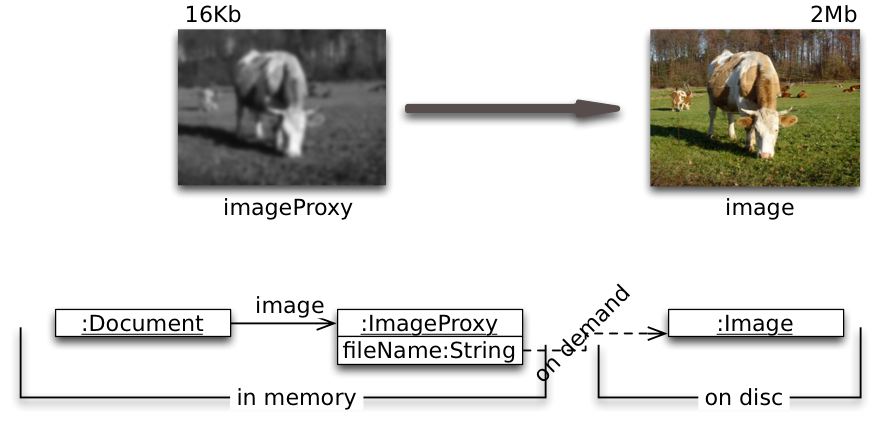
Virtual Proxies: Placeholders (as in image example).
Idea
Create expensive objects only on demand. Objects associated with a large amount of data in a file or database may only be loaded into memory if the operation on the proxy demands that they are loaded.
Implementation
Some subset of operations may be performed without bothering to load the entire object, e.g., return the extent of an image.
Smart References: Additional functionality.
Idea
Replace bare pointer and provide additional actions when accessed.
Examples
- Locking / unlocking references to objects used from multiple threads
- Reference counting, e.g., for resource management (garbage collection, observer activities)
Remote Proxies: Make distribution transparent.
Idea
Provide a local interface for communicating with objects in a different address space. Operations on the proxies are delegated to a remote object and return values are passed through the proxy back to the client.
Issues
From the client’s view, the proxy responds just like if the object were local, even though it is actually sending requests over a network.
(Network failures may be impossible to hide… LSP?)
Protection Proxies: Rights management.
Idea
Verify that the caller has permission to perform the operation.
Issues
- Different clients may have different access levels for operating on an object
- Read-only objects may be protected from unauthorized modifications this way
- Exceptions are thrown in such violation cases (LSP?)
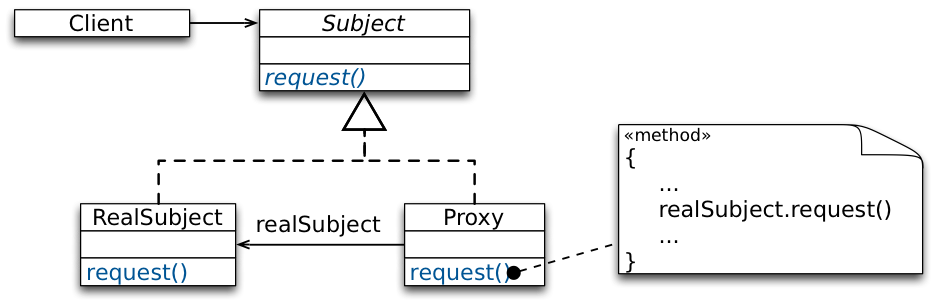
Structure
Example
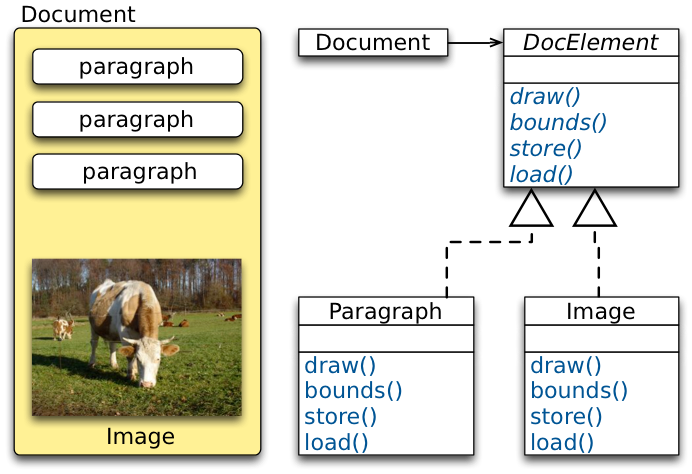
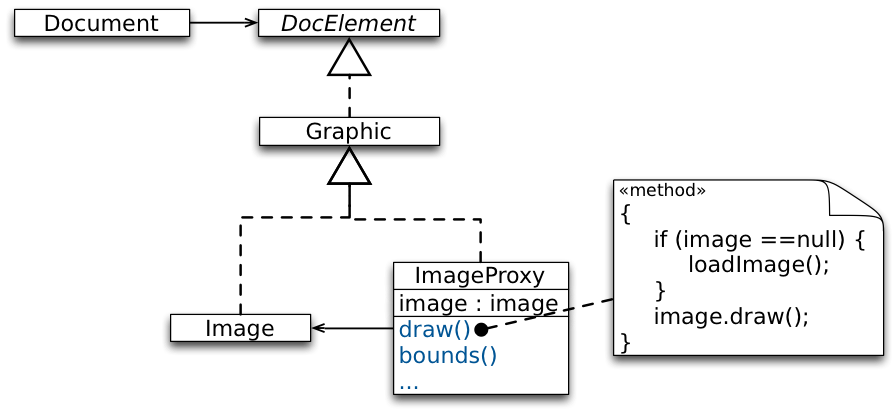
The Image Proxy
- implements the same interface as the real object.
Client code is unaware that it doesn't use the real object. - instantiates the real object when required, e.g., when the editor asks the proxy to display itself by invoking its
draw()operation.
Keeps a reference to the image after creating it to forward subsequent requests to the image.
Summary
Java's Dynamic Proxy Class
Questions
Delegation semantics would be desirable for a protection proxy, where the different methods have different protection levels. Without delegation semantics, we need to know the self-call structure of the RealSubject to make sure that we check for sufficient access rights.